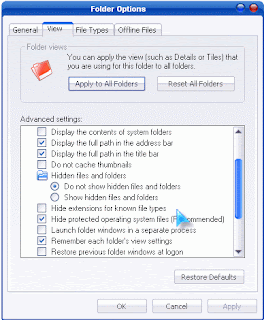
In order to boost sales, traders fake antivirus products such as Live PC Care offers direct technical support for their victims.
According to researchers at Symantec, once users install the program, they will see who preach the false appearance that their PC had been infected with some kind of malware. This is a common way to fake antivirus offering his services.
"What is unusual is that it is now a free trial version of Live PC Care provides the 'online support' to such notice," said Marc Fossi, manager of Development, Symantec Security Response, as VIVAnews quoted from PCWorld, February 23, 2010.
Fossi mentioned, with the click of a button, the user will be connected with an agent who will answer any questions users have about the product, via instant message.
"The agent script is not automatic, but a real person. This suggests the validity of these fake antivirus programs, "said Fossi. "Obviously, the user thinks, if the program has a real technical support, software would be nice," he said.
Nevertheless, the technical support provided did not help much. According to Symantec, the service staff just trying to convince the victim to buy a product costing 30 to 100 dollars.
This is not the first time detected a fake security products have technical support services. Previously, the company called Innovative Marketing has operated a call center to support the "security products" they like WinFixer.
According to some security analysts, technicians from the Innovative Marketing applies the same as Live PC Care, they try to convince victims to buy their product.
If you've purchased and installed, the 'virus' is sometimes lowered the security settings on the victim's computer. In addition, they offer a false sense of security because their product actually does not protect a computer from the latest security threats.
Fake antivirus itself has become a frustrating problem for users over the past year. Software is sometimes inadvertently installed through pop-up ads that appear and try to convince the victim that there is a problem on their PC.
During July 2008 until July 2009 then, Symantec itself has noted there are 43 million fake antivirus trial installation of the Internet user's computer.














 The answer is pretty simple. You have to take care of your pc and tweak a bit. Overclocking your PC is an option to try at your own risk which i don’t recommend hence not discussing in this post. You only have to understand why your pc is slowing down and do things to prevent from slowing down.
The answer is pretty simple. You have to take care of your pc and tweak a bit. Overclocking your PC is an option to try at your own risk which i don’t recommend hence not discussing in this post. You only have to understand why your pc is slowing down and do things to prevent from slowing down.